Implementing Attribute-Based Access Control (ABAC) for Enhanced Security in AWS
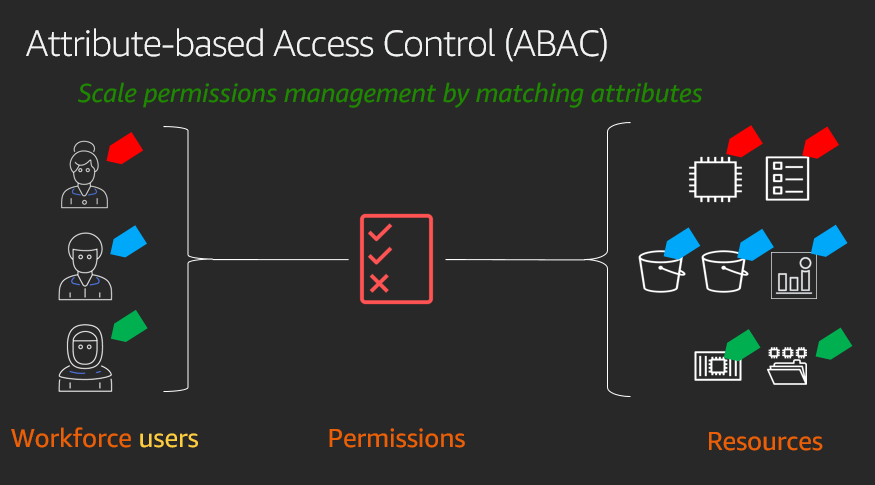
Attribute-based access control (ABAC) is an authorization strategy that lets you create fine-grained permissions based on user attributes, such as department, job role, and team name. User attributes make permissions more intuitive, and they simplify the administrative experience of managing access. By specifying permissions using attributes, you can reduce the number of distinct permissions that you need for creating fine-grained controls in your AWS account.
Attribute-Based Access Control (ABAC) is a security model that allows you to define access control policies based on attributes. In an ABAC model, access is granted or denied based on the attributes of the user, resource, environment, and any other relevant factors.
Amazon Web Services (AWS) provides several services and tools to implement ABAC. Here are some of the key components of ABAC for AWS:
1. AWS Identity and Access Management (IAM): IAM is a web service that allows you to manage users and their access to AWS resources. IAM allows you to create policies that define what actions a user can perform on which resources. IAM policies can use ABAC to grant or deny access based on attributes.
2. AWS Resource Groups: AWS Resource Groups is a service that allows you to create logical groups of AWS resources. Resource Groups can be used to organize resources based on attributes such as tags, regions, and other metadata. ABAC policies can be applied to Resource Groups to control access to all resources within the group.
3. AWS Security Token Service (STS): STS is a web service that provides temporary security credentials to users who request access to AWS resources. STS can be used to implement ABAC by issuing temporary credentials with specific attributes that are required to access certain resources.
4. AWS Key Management Service (KMS): KMS is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data. KMS can use ABAC to control access to the keys based on attributes such as user, time, location, and other relevant factors.
5. AWS Organizations: AWS Organizations is a service that allows you to manage multiple AWS accounts. ABAC policies can be applied to Organizations to control access to all accounts within the organization based on attributes such as user, role, and other metadata.
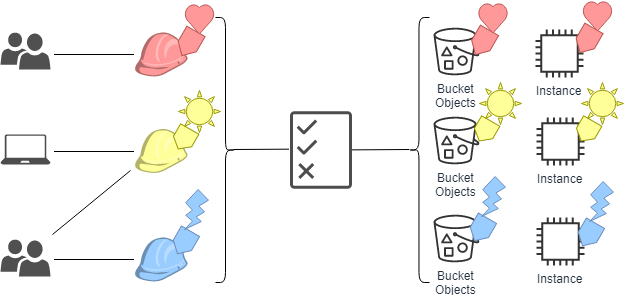
Instead of creating AWS Identity and Access Management (IAM) roles with distinct policies for every team or individual to ensure the right levels of access, you can use ABAC to group attributes to identify which resources a set of users can access. Then, as you add new users and resources, you can associate the appropriate attributes so that the right users have access to the right resources. It’s no longer necessary to update existing policies to allow new users to access resources. With attribute-based access controls, your authorization strategy can scale at the pace of your innovation.
Here are the key benefits of ABAC:
1. Simplify IAM role management: With ABAC, multiple users using the same IAM role can still get unique, fine-grained access because permissions are based on user attributes. You can define attributes in AWS, or you can pass user attributes from your existing identity provider (IdP) into AWS by using AWS IAM Identity Center (successor to AWS SSO), IAM, or Amazon Cognito. You than can author IAM policies to ensure that your users get access to only the AWS resources that have matching attributes. This approach helps you reduce the number of IAM roles you need for the use cases in your AWS account.
2. Apply fine-grained permissions as resources change: With ABAC, you grant access based on user attributes. You can use attributes you’ve assigned in AWS, or you can pass in attributes from your IdP and update user attributes in your IdP. Users with specific attributes can immediately access new resources that have matching attributes, which happens without you having to update users’ permissions.
3. Monitor actions that users have performed: When using ABAC, you can determine which identity is responsible for actions performed using IAM roles. For example, the IAM SourceIdentity attribute is logged in AWS CloudTrail for every action performed in AWS using an IAM role. With the SourceIdentity attribute set, you can connect the CloudTrail event with the identity of the user or application that performed the action. Even in the case of role changing, where a user uses one IAM role to assume another IAM role, you can determine which identity performed which actions.